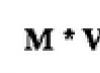Introduction
Expanding the capabilities of routers through alternative firmware is, of course, interesting. However, sometimes there comes a time when adding another add-on leads to the fact that the already “soaked” router stops working stably. In this case, you will either have to give up some of the functions, or be prepared to fork out money to buy a more powerful router model, or even a ready-made solution in the form of a small server with pre-installed software. But why? After all, you just need to take an old computer and configure everything you need yourself. This is what we will do. You can, of course, pick up a file and turn the locomotive into a fighter, that is, install some kind of Linux distribution (along the way, be sure to rebuild the kernel, where would you be without that), and then take a long and tedious time to bring it to the desired state, screwing Webmin or something like that.
We won’t split hairs and use the specialized distribution Zentyal. It has two important advantages for us. Firstly, it has a unified web interface for managing all the main server modules (routing, firewall, DHCP, mail, and so on). Secondly, it is based on Ubuntu, which means that the entire package base of this distribution is available to us. In fact, you can install all Zentyal components on Ubuntu from a special PPA repository. There is another, very similar product - ClearOS. Both distributions have different subscription options, but the free version is quite enough for us. If you wish, and for relatively little money, you can get a little more features, which is more relevant for organizations than for the home.
⇡ Preparation
The recommended configuration for Zentyal for a PC that will play the role of a server is approximately the following: a Pentium 4 level processor, at least one gigabyte of RAM, an 80 GB hard drive and at least two network interfaces (we will be making a gateway). In reality, it all depends on your tasks. The network component consumes the least resources, so it’s quite possible to get by with some kind of “atomic” machine. If you plan to install an antivirus, mail, filter, and so on, then, perhaps, you need to take something more serious. It is logical that you need to buy a Wi-Fi adapter (list of compatibles) if you need a wireless network, but as an alternative you can purchase an access point (bridge) - in some cases this is even better, since the server will probably be hidden in some quiet corner , that is, physically remote from the location where wireless clients gather. There’s no need to skimp on memory—it’s already quite inexpensive anyway. If you wish, you can organize a RAID, but there doesn’t seem to be much point in this. Built-in or software solutions are not so reliable, and a hardware controller would probably be a waste of money in our case. And yet, it would be wisest to allocate a separate hard drive for data (“file storage”, torrent downloads, etc.) or even add a USB drive. It is better to connect it after installing the OS.

⇡ Installation of Zentyal
When the machine is prepared, you will need to download the required ISO image of the installer from this page. We burn the ISO onto a disc or write it onto a flash drive. Along the way, you can register with Zentyal and get a basic subscription to additional services by clicking on the Subscribe button on the same page. We enable booting from a removable drive or CD drive in the BIOS, insert our media with the system image and reboot. If you want, you can select Russian during installation. In the menu, select the first item (delete all disk) and press Enter.



The installation wizard will guide us through all the main points. The first thing you need to do is set up your keyboard.




One of the network interfaces will look at the external network, and the other will look at the local network. By and large, it makes no difference which interface you assign to which role. In our example, eth0 will serve for local connection, and eth1 for Internet access.


If the installer was unable to determine your current time zone, then he needs a little help.


Then the installer will independently partition the disk, format it and install the base system. Finally, you will be prompted to create a new administrator account.


After this, the remaining OS components will be installed and we will be prompted to reboot. At the same time, we will return booting from the hard drive to the BIOS.

⇡ Basic setup
Zentyal is managed through a web interface, which is similar to the interface of most routers. From the local network it is accessible at https://ip_server/. After downloading, we are prompted to log into it using the administrator login and password that were specified during the installation stage. We can define one of the standard roles for the server (we need Gateway) or skip the setup and select all the necessary modules ourselves. This is done in the “Software Management” → “Zentyal Components” section. During installation, recommendations appear to install some other components that are not initially available. For example, when installing an antivirus and SAMBA (for sharing files over a network), it is recommended to enable the option to scan shared folders for malware. Already installed modules are enabled and disabled in the “Module Status” section. Please note that some services depend on each other - until you enable one of them, the other will not be available. Quick access to information about the current state of the system and the start (restart) of basic services is available from the main page of the web interface, also known as the “Desktop”. In the upper right corner there is a “Save Changes” button, do not forget to click on it after changing the settings.




When installing some modules, the setup wizard will be launched. For example, to configure network connections. For the external interface, options are available to manually specify all settings or receive them via DHCP or via VLAN (802.1q) or ADSL (PPPOE). Alas, at the moment there is no ready-made support for PPTP/L2TP, so beloved by our providers, and its implementation is not planned until the next release, which will be released in the fall. The simplest way out of this situation seems to be to buy a simple router (from 500 rubles), configure it to connect to the provider, register a static IP for the server and move it to the DMZ or completely forward ports to it. For the internal server interface, you must specify a static IP address and select a subnet mask. Then the settings can be changed in the “Network” → “Interfaces” section.


We will also need NTP, DNS, DDNS and DHCP modules. The first three are optional, but you can’t do without the last one if you don’t want to manually configure network settings on all machines on the local network. In any case, a local caching DNS server, an external domain, and a local time server are useful. Just remember to enable synchronization with third-party NTP servers in the “System” → “Date/Time” section. At the same time, you can register static routes, for example, to access the resources of the provider’s local network.



Now let's get acquainted with the concept of objects and services in Zentyal. Objects are any devices on the network or groups of them (PCs, printers, NAS, and so on). Initially, lists of objects (groups) are created, to which the required IP addresses or address ranges are then added. You can also specify a MAC address for a specific host.




Services in Zentyal's understanding are ports or groups of ports and protocols. When creating a service, you can check the “Internal” checkbox if this port and protocol are used on the server (for example, port 21 for the Zentyal FTP server). Similar to objects, each service can include a whole list of ports/protocols. Services and objects can later be used in other modules such as a firewall, and they are needed only for more flexible and simpler network configuration.


In general, to activate DHCP, it is enough to set the same settings as in the first screenshot below. After this, you must add ranges of IP addresses that will be distributed to the machines - you can create several of them at once for different groups of devices. Static DHCP is implemented using objects. A little higher in our example, we created a list of wire objects, in which we specified several machines with IP and MAC addresses. So, we just need to add any list of objects in the “Fixed Addresses” section so that computers from this list are assigned pre-specified IP addresses in accordance with their MAC addresses.



The firewall is divided into two logical parts. The first, the packet filter, is not so interesting, since it only allows you to configure the behavior of internal Zentyal services. The second part is the most common port forwarding.


As an example, let’s open access to the Zentyal web interface from the outside by adding one rule to the “Filtering rules from external networks on Zentyal”.

Bandwidth distribution is configured in Gateway → Traffic Shaping. Naturally, this module must already be installed. First of all, in the “Interface Speeds” section, you need to indicate the maximum incoming and outgoing speeds according to your tariff. Speed control is based on the L7 filter system. In the Application Protocols section we can create and edit protocol groups. Then you need to add the necessary rules for each of the interfaces, setting the priority and setting the speed indicators. In particular, you can set a limit for each computer on the local network. The features of setting up QoS have already been discussed in this article - it is recommended that you read the relevant section.





If you have several external channels for accessing the Internet (for example, two gateways or two ADSL modems, not necessarily with the same speed), then you can configure traffic balancing. In the “Network” → “Gateways” section these channels are registered, and for PPPOE and DHCP they are created automatically. For each external connection, you can specify a weight, that is, in fact, the priority of choosing a particular channel. If the speeds of the external channels are the same, then the weights should also be the same. Otherwise, the higher the priority number (greater than 1), and therefore the lower the speed, the less often it will be accessed. Balancing itself is based on rules in which you can specify through which gateway and what data will go. This is where objects and services will come in handy once again.


Having several gateways at once provides another advantage - the ability to automatically switch between them if one of them stops working. But first, let's get acquainted a little with the Zentyal event system. We are interested in the “Failover WAN” event, which must be enabled. Some events have configurable parameters, for example, you can specify the percentage of free space on your hard drive, upon reaching which an alert will be generated. An event notification can be delivered to the administrator in several ways - for us, only RSS or a message in Jabber are relevant. At the same time, all event logs are recorded in logs, which can then be viewed in the appropriate section.




So, after enabling the fault-tolerant WAN, go to the “Network” section and go to the item called exactly the same. Here we add rules to check the health of each gateway by “ping” the gateway itself, any host, an HTTP request, or a DNS request. Immediately add a check launch interval and set the number of attempts. If a gateway fails the test, it is temporarily disabled until it is restored to functionality, and all requests are automatically redirected to another gateway(s).

Additional settings
If you decide to sign up for a basic subscription to Zentyal services, you should have received a login and password by email. Before connecting it, you need to generate certificates (digital keys) in the “Certification Center”. We will need them later to create VPN connections to the server. For a root certificate, it is enough to indicate the name of the organization and its validity period. After that, in the “Subscription” → Server Subscription section, just enter the sent login and password. To be honest, there is no particular point in this - you can only look in demo mode at the features available in paid subscription options (backup, managing a group of servers, remote updating, and so on).


In the “System” → Import/Export Configuration section, you can save and restore the current server settings. It is recommended to download the settings file and save it on another machine or removable storage device. You can also save the configuration in the Zentyal service. This is perhaps the only benefit from it, besides the ability to see whether the server is currently online, and automatic notification by mail if it suddenly goes offline.


Finally, the last thing that is recommended to be done during the initial setup is to update the system from the “System updates” section by clicking on “List of updates”, checking the required packages and then clicking “Update”. A little advice - it’s better not to select all the packages en masse, but to update them in small batches. An alternative option is to simply run two commands in the User Console:
sudo apt-get update && sudo apt-get upgrade
Finally, turn on automatic software updates in the settings.


Let's stop here, perhaps. In the next part we will look at creating groups and users, setting up a file hosting service, installing a torrent client and a number of other things.
Several years ago, in the IT market, suddenly (or maybe not suddenly) suppliers of “heavy” software, “heavy” equipment and “heavy” IT services suddenly began to unanimously swear that steel was now very important for them consumers belonging to the category “Medium and Small Businesses” (SMB) and now they, based on their Enterprise products (that is, products aimed at large corporations), will produce SMB products - that is, products addressed to medium and even small businesses .
There was even (somewhere in St. Petersburg) a special large-scale multi-vendor IT conference, at which well-known domestic and foreign IT companies voiced their plans to capture the SMB segment of the Russian IT market. But what is noteworthy: almost none of the speakers at this conference drew even approximate boundaries between large (Enterprise), medium (Medium), small (Small) and very small (SoHo) customers (clients). Moreover, all questions regarding this border were answered very evasively. The range of answers was as follows: from “Everyone knows this” to “Each company has its own boundary.”
I had a chance to talk on the sidelines at that IT conference with a well-known analyst. Among other things, I asked him the following question: “Where, in your opinion, is the border between large and medium-sized businesses?” He said: “This is a very interesting question. In my notebook there are about two dozen possible answers to it.” However, he refused to publish (and even voice) these options. Jokingly noting that this is a kind of know-how.
The processes of shifting the “horizontal” focuses of IT enterprises continue to this day. Both Enerprise solution providers and companies that previously focused primarily on the SoHo segment are looking at the SMB segment. Therefore, the problem of a unified “border” terminology, in my opinion, continues to remain relevant. In this regard, I was very pleased with the presentation of the results of Lenovo’s work that took place yesterday (both in the world and in Russia). Among other things, it outlined the boundaries between those categories of consumers that the company identifies for itself.


In my opinion, this is a very correct gradation. What about yours?
Testing methodology
For testing, routers used in small office networks were selected. Necessary conditions when selecting devices were support for operation in Fast Ethernet networks at a speed of 10/100 Mbit/s and the mandatory presence of a WAN port for connecting a cable or xDSL modem. At the same time, no restrictions were set on the number of LAN and WAN ports, or on overall dimensions and prices.
The routers were tested in three stages. At the first stage, the throughput of devices when transmitting data via the TCP protocol was assessed, at the second stage - via UDP, and at the third stage, the data transfer speed was measured via the FTP protocol. The testing stand consisted of three workstations of the same configuration, two of which were connected to the switch built into the router via LAN ports and configured to work on a local network, and the third workstation imitated an xDSL modem and was accordingly connected to the WAN port.
Workstations configuration:
Operating system Windows XP Professional SP1;
Motherboard Fujitsu Siemens D1521 (i845 GE);
Central processor Intel Pentium 4 with a clock frequency of 2.4 GHz;
Random access memory (RAM) 256 MB DDR;
Hard disk (HDD) Samsung SP0411N 40 GB.
Router performance testing was carried out using special software NetIQ Chariot version 4.4, developed specifically for testing network equipment. The functionality of routers was also considered: the informativeness of port status indicators and the ease of connecting and configuring the router, etc. When considering the design of the router, we primarily took into account the correspondence of the number of ports and the size of the device, the convenience of the location of the indicators, the possibility of wall mounting the switch, and only lastly the appearance of the device.

Bench installation diagram for testing routers
The calculated quality indicators were used to select the highest quality router: the higher the router’s integral quality indicator, the better its quality. If you divide the integral indicator of a device’s quality by its price, the resulting quality/price ratio shows how profitable it is to purchase a router, that is, the highest quality/price ratio corresponds to the optimal purchase.
Test results
The test results are shown in the table. As can be seen from the results, different router models show different values of network traffic, which indicates the use of different element base in these devices.

Router testing results

TCP testing results

UDP testing results

FTPput testing results

FTPget testing results
Editor's Choice
The selection of test winners was carried out in two categories: “The highest quality router” and “Optimal purchase”. The router won the “Best Quality Router” category TRENDnet TW100-BRV304. The winner in the “Best Buy” category was the router SMC 2804WBR.
Test participants
Edimax BR-6104, BR-6524 and BR-6541
Edimax routers BR-6104, BR-6524 and BR-6541 are positioned as SOHO class devices and are designed for organizing small local networks.
These devices allow you to organize high-speed Internet access using a cable or DSL modem for workstations connected to the built-in switch via the Fast Ethernet protocol with a bandwidth of 100 Mbit/s. At the same time, according to technical documentation, the data transfer speed between WAN and LAN ports is limited to 20 Mbit/s.
Additionally, by connecting a switch to the router, it is possible to organize a network with up to 253 workstations. To simplify the network settings of the local network, routers have a built-in DHCP server that allows you to assign IP addresses automatically, without resorting to the settings of the network cards of each workstation. Devices can be connected to an external network via the WAN port using the following settings:
Dynamic IP address (Dynamic IP) - used when connecting via a cable modem and communicating via a telephone line;
PPTP is used to organize a point-to-point connection;
Fixed IP address (Static IP) - used when connecting an ADSL modem when the provider has issued a permanent IP address;
The operation of routers is based on NAT (Network Address Translation) technology, which allows you to translate all requests with addresses from the local internal network to an external one, substituting the external IP address of the router’s WAN port in the request header.

NAT makes it possible to configure a virtual server, which can make one of the workstations connected to the local network behind the router visible to the external network. To do this, just assign the port and address of the local machine to which the request will be sent. In addition, NAT allows you to work with applications that use bidirectional data exchange protocols (network games, video conferencing, IP telephony).
The required level of network security and local network protection from unauthorized access is provided by the built-in Firewall software security settings.
At the same time, Firewall allows you to configure such a level of access when you can open ports for working with email, FTP and the Internet, install protection against external attacks by hackers (Hacker Prevention), and also configure demilitarized zones (DMZ) that allow access to a specific workstation from the external network.
The Edimax BR-6104 router has four LAN ports for connecting workstations and switching devices and one WAN port for connecting a cable or ADSL modem, and the modem can be connected either with a direct or an RJ-45 crossover cable. This device uses the classic scheme of organizing a local network with Internet access.
The Edimax BR-6524 router, like the previous model, has four LAN ports for connecting computers and switches, but is also equipped with two WAN ports for connecting to a cable or ADSL modem, which naturally increases bandwidth. Modems can be connected using a straight or crossover cable.
The Edimax BR-6541 model has four WAN ports and one LAN port. This implies connecting a separate switching device with an internal local network or a working server (for example, FTP) to the LAN port, since using one workstation and connecting to the Internet over four high-speed channels is impractical.
SMC 7004VBR
Our testing involved multifunctional SMC Networks routers from the Barricade family, which allow you to organize a local network with Internet access, provide shared access to printers and corporate information, while providing the necessary level of protection.
The first device we tested was the SMC 7004VBR model - the simplest solution in the Barricade family, but at the same time meeting all the necessary requirements for SOHO class routers. The SMC 7004VBR device is positioned by the manufacturer as a broadband Cable/DSL router capable of running Windows, Linux, Mac OS, Novell NetWare, etc. operating systems.
The SMC7004VBR model is equipped with four 10/100 Mbps ports with automatic connection speed detection, used to connect workstations or switching devices with an RJ-45 cable. The WAN port, located, like the LAN ports, on the back of the device, is designed to connect a cable or xDSL modem and provides Internet access for up to 253 users within the local network.
A SOHO computer network is a small local network that can connect computers, TVs on the Smart TV platform, digital video cameras, players, and so on. The emergence of televisions with Smart TV technology capabilities made it possible to connect them to a wireless (Wi-Fi) or cable local (Ethernet) network, which changed the quality of services provided by the SOHO computer network.
Smart TV provides digital terrestrial broadcasting DVB-T, digital cable broadcasting DVB-C, digital satellite broadcasting DVB-S. In addition, Smart TV technology allows you to connect your TV to the Internet and use its various features. A Smart TV connected to the Internet allows you to watch videos from YouTube, surf websites using a full-fledged web browser, and communicate on social networks Facebook and Twitter.
In Smart TV you can use instant messaging tools (messengers) - Google Talk and Skype. When you turn on the Smart TV mode, the SmartHub graphical interface appears on the screen (analogous to the desktop on a PC), which displays icons of the specified applications and widgets.
In Smart TV, you can record TV programs from the TV to an external hard drive via a USB port and watch videos from the hard drive or flash drive. In addition, on the TV you can view photos, videos and play music from devices connected to the SOHO local network. A Smart TV is capable of playing HD and 3D videos and can convert 2D images into 3D images. You can install various widgets (gadgets or informers) and applications from Samsung Apps on your TV. After registering your TV (using a PC) at http://www.divx.com/en/movies/register-your-device, you can watch DivX videos on your TV.
To create a SOHO-type computer local network with Internet access, you can use Wi-Fi technology. Wireless routers are widely used to create wireless networks with Internet access. For example, a wireless router like LinksysWRT160N. You can connect not only wireless devices to it, but also connect devices with an Ethernet port (RJ-45) via cable. For a standard Ethernet connection to the provider, the router is equipped with an Ethernet WAN port.
As an example, the figure shows the LinksysWRT160N wireless router (in Gateway mode), on the basis of which a SOHO wireless network with Internet access is implemented. A desktop computer (MY), a laptop (HOME) and a TV on the Smart TV UE32D6500 platform are connected to the local network. The DHCP server built into the router assigns dynamic private IP addresses to MY and HOME computers and the UE32D6500 TV in local networks (WLAN and LAN) in the range 192.168.1.100 - 192.168.1.149.
A router (local IP address or private network router IP address - 192.168.1.1) with IP address translation (NAT) functionality provides translation of private IP addresses of local networks (WLAN and LAN) to the external global IP address. The external global IP address is assigned by the Internet service provider. The SOHO network diagram is shown in the figure.
Information exchange (sharing of folders and files) between notebook (HOME) and desktop (MY) is carried out over the local network from the HOME and MY computers. From the TV over a local network, you can view photos and videos that are located on the hard drives of your PC. A router with an IP address translation (NAT) function, connected via an Ethernet WAN port to the Internet, provides computers (HOME and MY) and the UE32D6500 TV with shared access to the Internet using the same IP address allocated by the provider. Thus, from a PC and TV, you can surf the Internet on websites using a web browser and watch streaming videos.
Selecting equipment for SOHO networks
- Son, what are you doing?
- I’m tacking over TV network, Mom.
Introduction
For many years now there has been a rapid development of computer technology, and one of its main branches is computer networks (Ethernet, Fast Ethernet, Gigabit Ethernet). They provide us with a huge number of services and opportunities: sharing of expensive resources (file servers, printers, modems), improving access to information (Internet, e-mail, teleconferencing, e-commerce, the ability to exchange data between different operating systems), freedom in geographical location computers.
In our country, the most widespread network technology is Ethernet (Ethernet, Fast Ethernet, Gigabit Ethernet). The basic principle underlying Ethernet is random access method to shared data transmission medium (CSMA/CD). Such a medium can be thick or thin coaxial cable, twisted pair, optical fiber or radio waves.
This article was prepared not for professionals, but for those who are going to create their own small network in the office or at home. In this article, we will only consider creating networks using thin coaxial cable and twisted pair.
Source equipment
Thin coaxial cable: diameter ~5 mm, thin inner conductor ~0.89 mm, resistance - 50 Ohms. The RG-58/U cable has a solid inner conductor, the RG-58 A/U cable has a multi-core conductor. Operating frequency - 10 MHz. A BNC connector is used to connect the cable to the equipment.
Example networks on coaxial cable:
rice. 1
Twisted pair cable (TP, Twisted Pair) comes in two types: shielded twisted pair (STP, Shielded Twisted Pair) and unshielded twisted pair (UTP, Unshielded Twisted Pair). It is also divided into single-core and multi-core twisted pair, as well as twisted pair for external installation.
Unshielded Twisted Pair: divided into categories 1,2,3,4,5,5e,6; the most common are 3 and 5, with data transfer speeds of 10 and 100 Mb/s. The cables are available in 4-pair versions. All pairs have a certain color and twist pitch. Typically, two pairs are for data transmission and two are for voice transmission. RJ-45 plugs and sockets are used to connect the cable to the equipment. Cable diameter: 22 AWG, 24 AWG, 26 AWG. The larger the number, the smaller its diameter.
Shielded Twisted Pair: divided into categories 5,5e,6,7. The main purpose of these cables is to support high-speed protocols. Shielded twisted pair cable protects transmitted signals well from external interference and is used only for data transmission.
Advantages and disadvantages of twisted pair: pros: Easy to install, fault-tolerant, high performance. Minuses: Limited length, poor immunity to interference (power transformers, transmitting devices, fluorescent lamps).
Table 1. Physical layer parameters for Ethernet, Fast Ethernet networks
Sockets for RJ45 plugs of categories 3 and 5 exist in various designs: wall-mounted and for mounting in boxes with a depth of 25 mm, 32 mm and more. To fasten plugs and sockets, the following minimum set of tools is used: Stripping tool - stripping, Crimping tool - crimping plugs onto a cable, Punch Down tool - sealing a cable into sockets and patch panels.
Patch panels - used for switching computer and telephone networks in structured cabling systems. There are at least 8 types: from 1 to 5 categories for 12, 16, 32, 48 or more ports for mounting in a 19" rack, shielded or not, with shutdown and monitoring. Internal connectors: 8-pin KRONE or 8 -pin 110 IDC (insulation interrupting) connector. Example operation of the patch panel as part of the network:

rice. 2
Network adapters.
I would like to say a few words about the main network adapters sold in our country.
Network adapters from Genius 10 MB (GE 2000 ISA and GE 2500 PCI) and 10/100 MB (PCI) are well suited for creating small (30-40 computers) networks with a length of each segment of no more than 60 meters.
D-Link products have a wide range of applications: from single and multi-processor network adapters with 10 MB (DE-528) and 10/100 MB (DE-538TX) management to multi-port print servers (DP-100 10 MB and DP-300 series 10/100 MB) and network management devices (hubs, switches, etc.) at a very affordable price.
3Com is known for its equipment that runs much faster and over longer distances than equipment from other manufacturers. The 509 ISA and 905TX 10/100 MB series network adapters are well known. These adapters have high performance due to the use of the latest data forwarding technologies: Parallel Tasking, Parallel Tasking II and Resilient Server Links, and management protocols: DMTF, RMON, RMON-2, SNMP, SNMP-2, dRMON, which reduce processor load and Improve application performance through more efficient data transfer across the ISA and PCI bus.
Currently, 3COM network adapters are mainly represented by cards of the 905 series:
- 3COM 905B-TX-NM - 10Base-T, 100Base-Tx. WOL. Supports all OS.
- 3COM 905C-TX-NM - differs from the previous model only in the absence of WOL.
- 3COM 905B-COMBO is an adapter that supports 10Base-T, 100Base-Tx, 10Base-2, 10Base-5 standards.
- 3COM 905B-FX is a network card for 1300nm multimode fiber optic cable.
For server solutions, the 3COM980C-TXM board is available. It uses unique Dynamic Access technology, which performs intelligent functions and helps solve problems that arise in information systems (load balancing, restoration of network connections, self-healing drivers, multiple virtual LANs, etc.).
Concentrators (hubs)
In all modern local network technologies, a device is defined that has several equal names - a concentrator, a hub. A hub combines separate physical network segments into a single shared environment. The main function of the hub is frame repetition on all ports.
A 10Mb Ethernet hub typically has from 4 to 72 ports, with the main part dedicated to connecting twisted pair cables. They are divided into 10Base-T and 100Base-Tx technology hubs, with support for 10Base-2 and 10Base-5 standards or not.
100Base-Tx hubs can be of two types: 100 on all ports simultaneously, or DualSpeed (10/100 MB) - when each port operates on auto-sensing 10/100 in isolation from the others. Sometimes hubs have a separate MDI port (uplink) for connecting hubs to each other.
Hubs are divided according to their design into hubs with a fixed number of ports and stacked hubs. Stacked hubs differ from fixed ones in that stacked hubs have special ports and cables for combining several hubs into a single repeater.
To create inexpensive 10 megabit networks with minimal load, Genius hubs with 8 (GH4080 SE) and 16 (GH4160 SE) ports are well suited.
Line of hubs from D-Link: DE-812TP, DE-816TP, DE-824TP - 10 Mbit hubs.
DFE-908Dx, DFE-916Dx - inexpensive and reliable 100 Mbit Dualspeed hubs for 8 and 16 ports. Hubs can be stacked up to 5 times, respectively, supporting up to 80 ports.
3COM offers a wide range of concentrators:
- Office Connect Ethernet Hub 4, 4C, 8, 8C, 16, 16C - 10 Mbit hubs. The number means the number of ports, the index "C" is the port for 10Base2 connection.
- OfficeConnect Fast Ethernet Hub 4, 8, 16 -100 Mbit hubs.
- OfficeConnect Dualspeed Hub 4, 8, 16 - 10/100 Mbit hubs.
- Super Stack II class hubs for 12 and 24 ports, stackable 4 in a stack. Etc.
Compliance with the numerous restrictions and tolerances set forth in the various Ethernet physical layer standards ensures that your network operates correctly. The most important limitations are related to the length of an individual cable segment, as well as the number of repeaters and the overall length of the network.
The “5-4-3” rules for coaxial networks and “4 hubs” for 10 megabit networks based on twisted pair provide a guarantee of network functionality. The “5-4-3 rule” says that a network can have no more than 4 repeaters and, accordingly, no more than 5 cable segments. Only 3 out of 5 segments can be loaded, that is, those to which end nodes are connected. In Fig. An example of an Ethernet network consisting of three segments connected by two repeaters is given. The “4 hubs” rule shows that between any two network nodes there should not be more than 4 repeaters. In Fig. Figure 3 shows a 10Base-T network with a maximum hierarchical connection of Ethernet hubs.

rice. 3
Compared to Ethernet networks, the length of a Fast Ethernet network is more severely limited. The “4 hubs” rule becomes a “two hubs” rule and the network diameter is reduced to approximately 200 meters. Moreover, repeaters must be connected to each other by a cable no longer than 5 meters.
Due to the fact that 3Com network cards have a shorter signal delay time after a collision occurs than others, sometimes problems arise when working with other network cards, a typical example is 1C Accounting version 7.5 and higher. In such cases, a switch helps solve the problem.

rice. 4
Switches
Recently, there has been a clear trend of replacing hubs with switches from the lower levels of networks. And this is not without reason. After all, switches are engaged in dividing the common shared environment into logical elements that represent independent shared environments with a smaller number of nodes. A network divided into logical segments has higher performance and reliability.
The main advantages of using the switch:
- in half duplex mode, the collision domain is localized between the switch port and the network card;
- it becomes possible to use full duplex mode;
- overcome network distance limitations;
- Network segmentation reduces the number of collisions in each segment, thereby increasing throughput.
An inexpensive and at the same time reliable solution is to use 3COM switches - OfficeConnect Dualspeed Switch 4, 8, 16 - with auto-sensing 10/100 for each port.
In Fig. Figures 5 and 6 present two cases of using switches in small networks. In the first case, the switch acts as a connection to an entire section of the network, and in the other as a division of the environment.
 |
 |
| rice. 5 | rice. 6 |
Conclusion
Currently, the transmission medium used in office LANs is predominantly Category 5 unshielded twisted pair (UTP). Connecting computers to a network using the set of tools described above usually does not cause difficulties due to the logical simplicity of the traditional star topology used in Ethernet networks.
A star topology is a topology that involves a radial connection between central and peripheral devices.
That is, in the area of the territorial center of the office, a hub or switch is installed with the required number of ports. Cable lines are laid from it to the workstations. Very often, in order to simplify the installation of networks and reduce the cost of construction, wall sockets are not installed, and the wire from the hub or switch is directly connected to the computer’s network card. This concludes the construction of the local network. In the best case, the cable is laid in a box; in the worst case, the cable is laid along the walls or attached with improvised means (staples) to the baseboard.
When laying the network, the following features must be taken into account:
- whether the number of users will increase or not;
- if the number of users is increased, then in what “geographical” coordinates of this company they will be located;
- whether the existing network traffic will be sufficient in the future;
- will there be a need to logically divide the network using a router, etc.
In such cases, the question arises about the correctness of the network laying, and if it was laid without complying with basic network standards, then the entire network has to be laid over again. Accordingly, overhead costs increase. Therefore, correct installation of the network will not only guarantee the operability of the network, but will also make it possible to modernize or expand it without affecting the original cable system.
We must not forget about the limitation on the length of each segment, which consists of several components: no more than 90 meters for horizontal wiring, and approximately 2 or 3 meters for patch cords. When crimping cables into RJ-45 plugs for category 5, you must follow the rule: leave a straight, untwisted cable no more than 13 mm. Also, for crimping into RJ-45 plugs, it is necessary to use plugs that correspond to the type of cable: for a multi-core cable, plugs with I-shaped blades are used, for a single-core cable, plugs with Y-shaped blades are used. Otherwise, there will be no guarantee that the cable will work correctly.
Thus, after all of the above, the criteria for choosing equipment for the network become clearer. Of course, a lot is left beyond the scope of this article: issues of setting up operating systems, resolving conflicts between equipment from different companies, and a review of a tool for installing and testing a network. But we did not consciously strive for this, but only wanted to give a general idea of the topic.